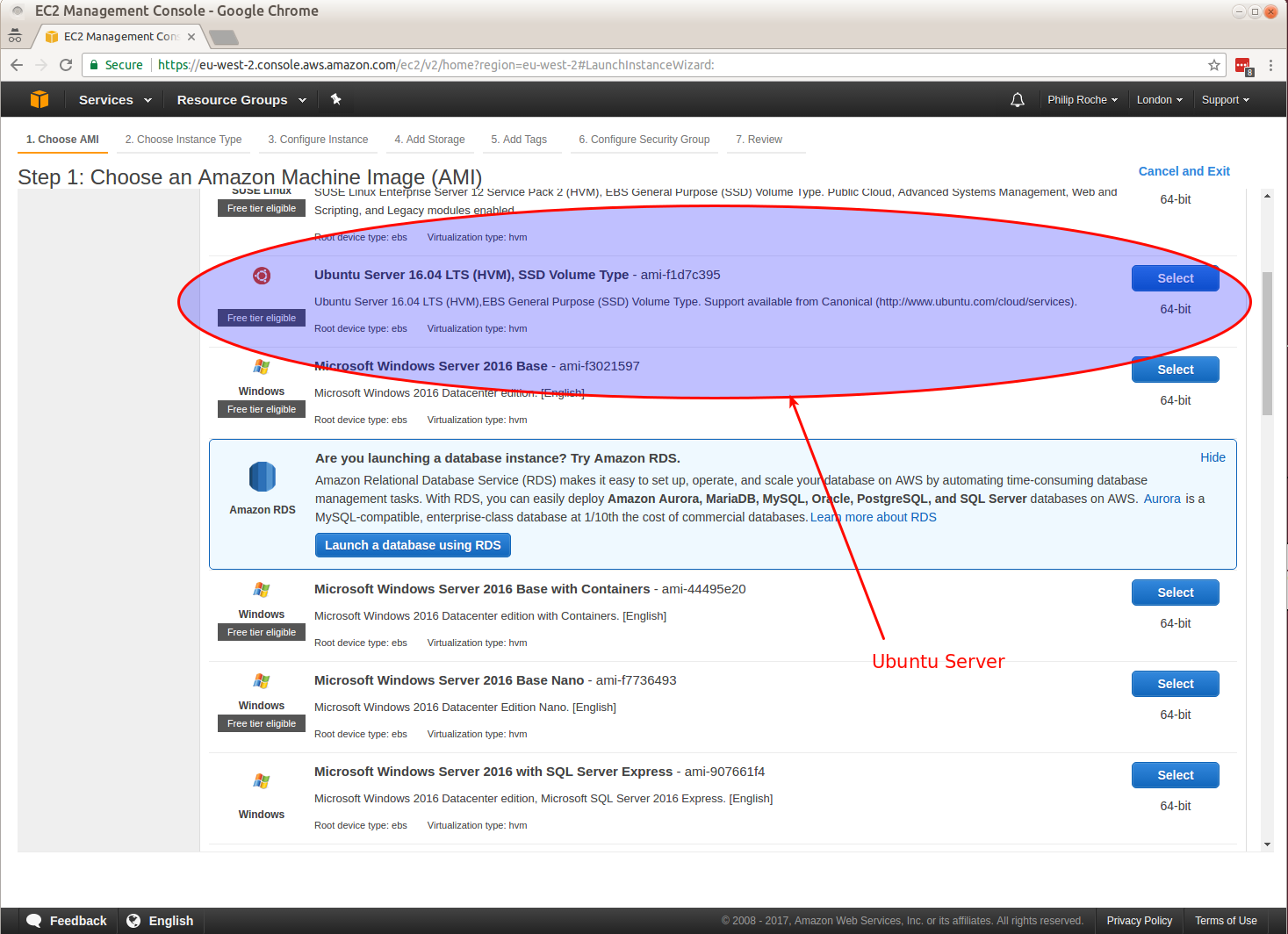
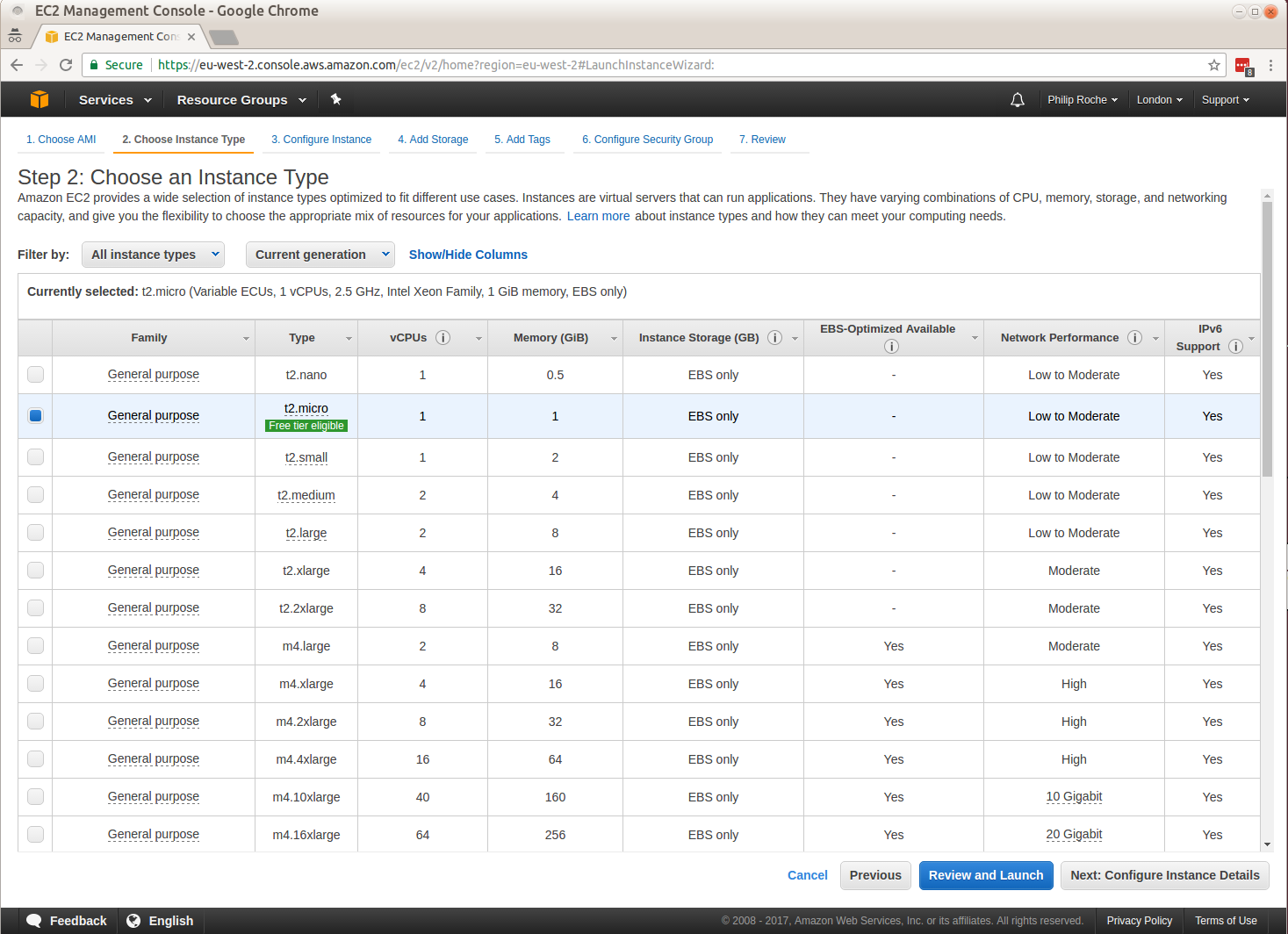
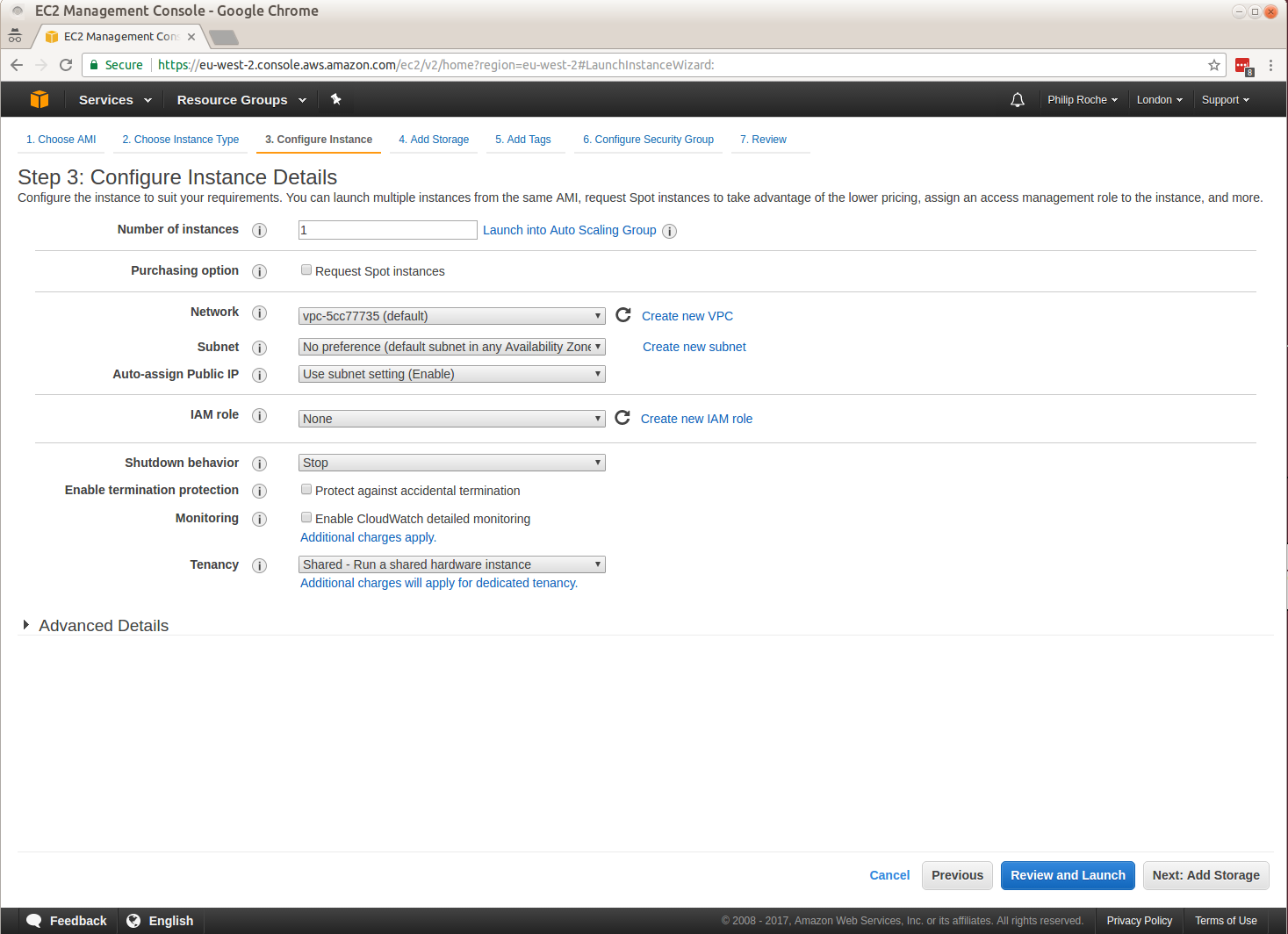
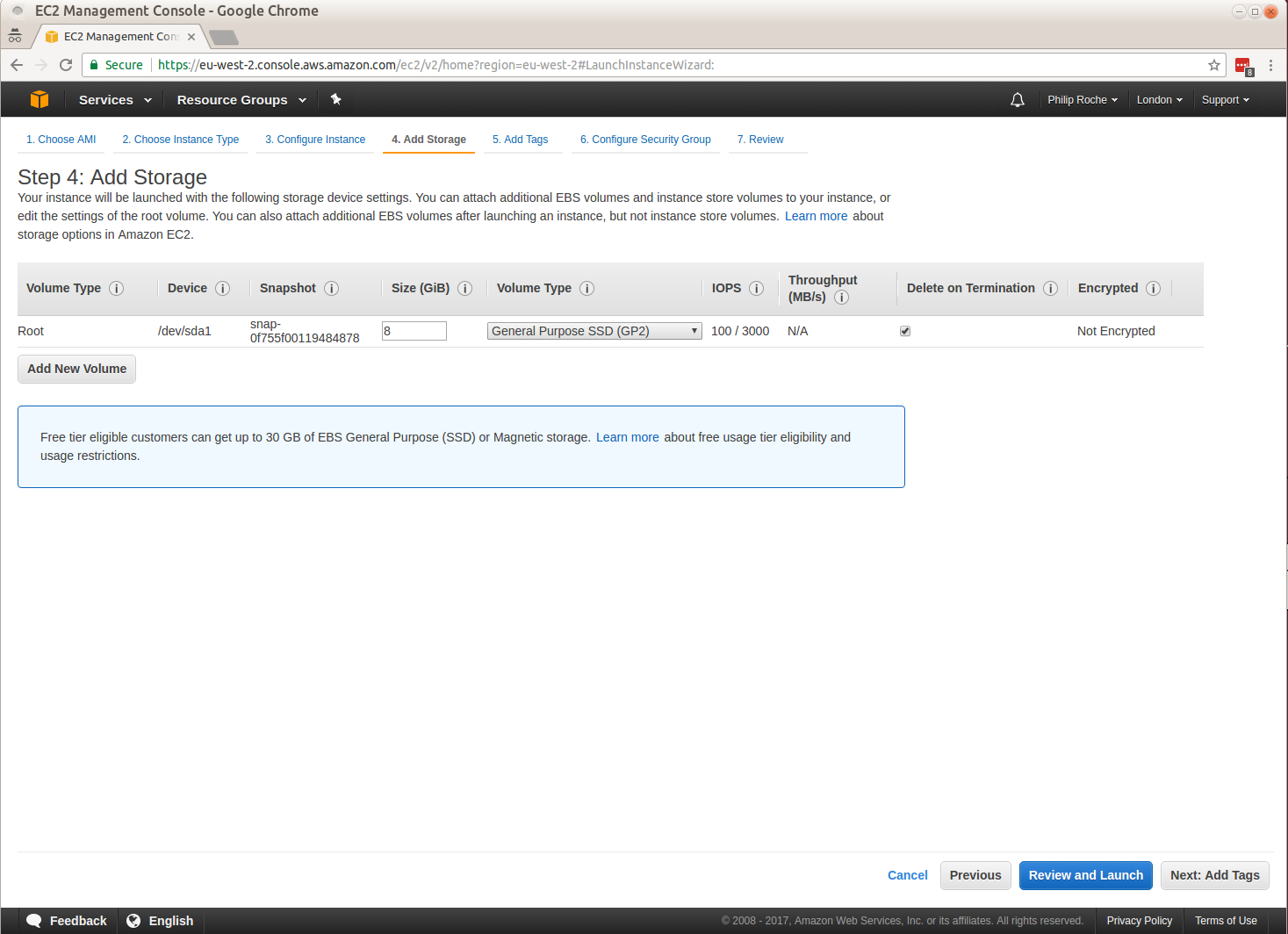
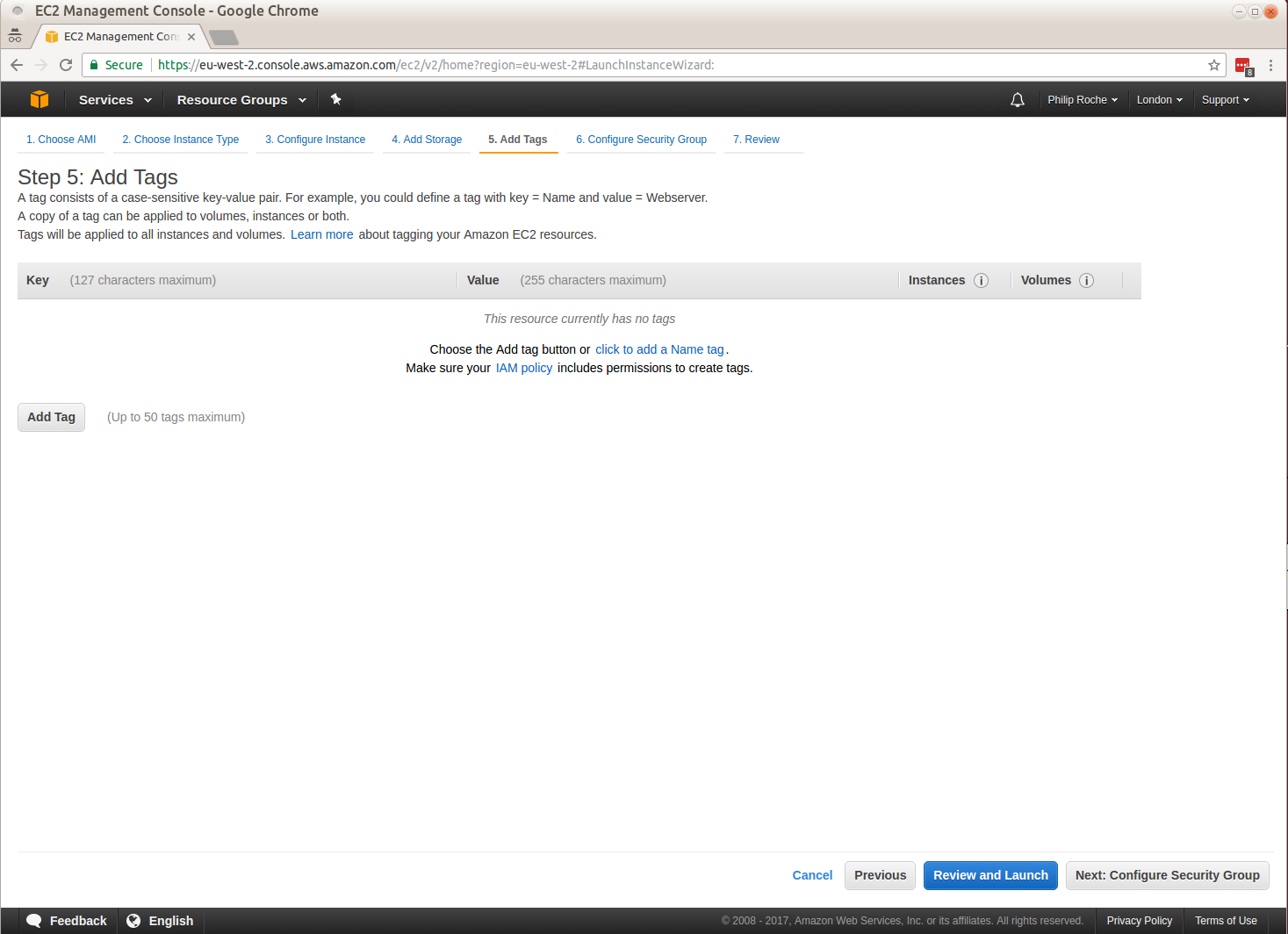
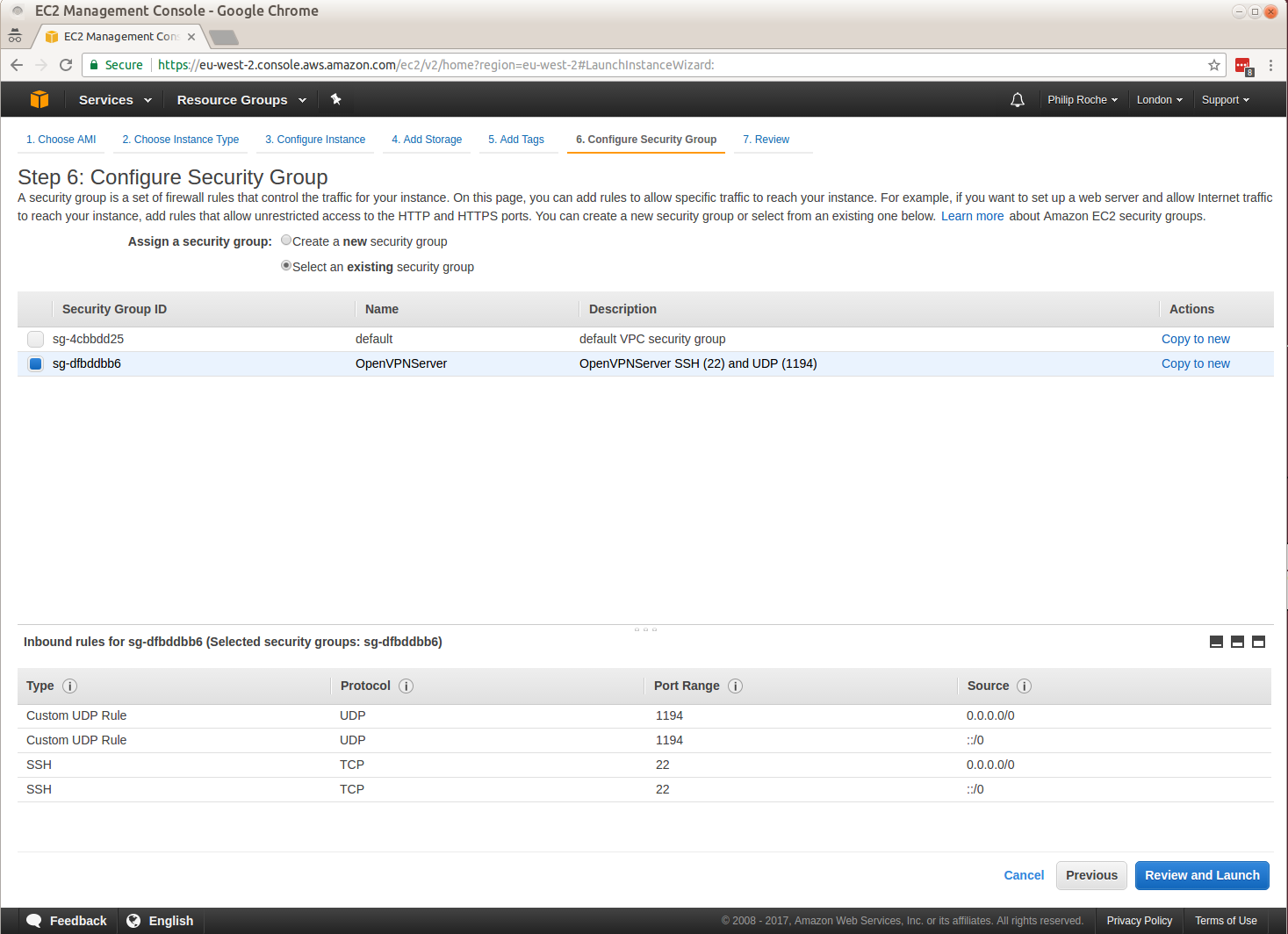
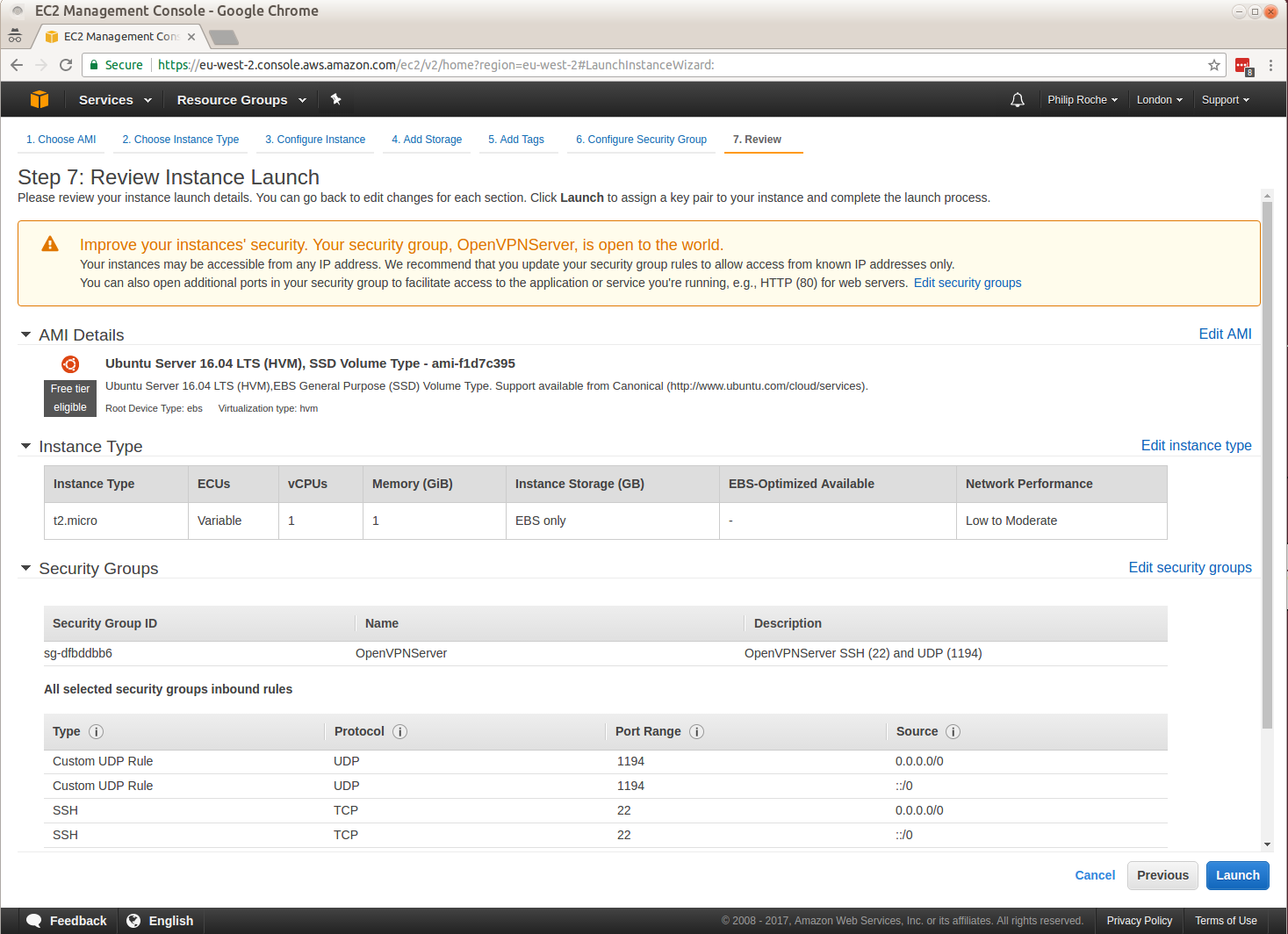
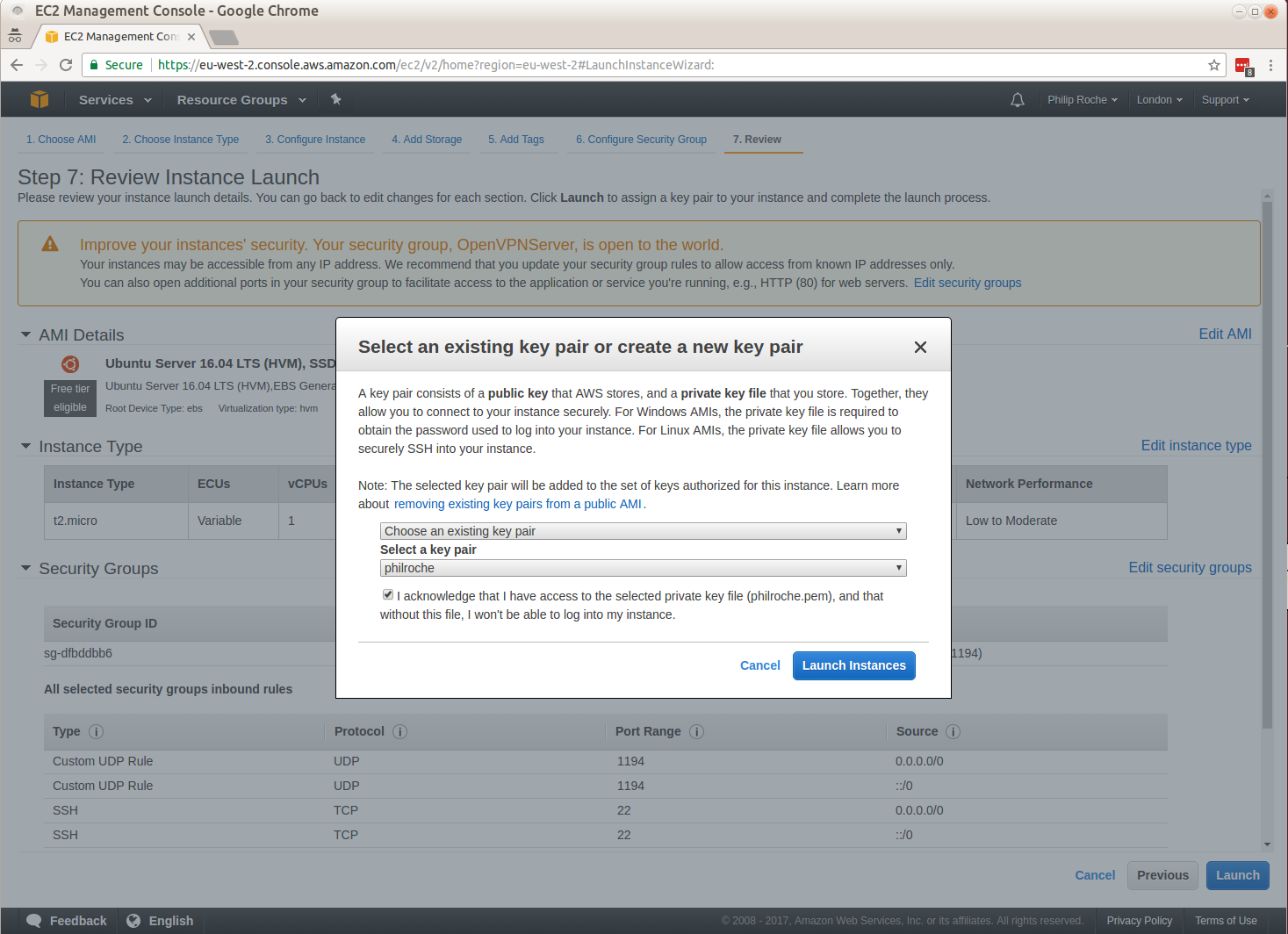
I work on the Canonical Public Cloud team and we publish all of the Ubuntu server images used in the cloud.
We often get asked what the differences are between two released images. For example what is the difference between the Ubuntu 20.04 LTS image kvm optimised image from 20200921 and the Ubuntu 20.04 LTS image kvm optimised image from 20201014, specifically what packages changed and what was included in those changes?
For each of our download images published to http://cloud-images.ubuntu.com/ we publish a package version manifest which lists all the packages installed and the versions installed at that time. It also lists any installed snaps the the revision of that snap currently installed. This is very useful for checking to see if an image you are about to use has the expected package version for your requirements or has the expected package version that addresses a vulnerability.
Example snippet from a package version manifest:
<snip>
python3-apport 2.20.11-0ubuntu27.9
python3-distutils 3.8.5-1~20.04.1
</snip>
This manifest is also useful to determine the differences between two images. You can do a simple diff of the manifests which will show you the version changes but you can also, with the help of a new ubuntu-cloud-image-changelog command line utility I have published to the Snap store, determine what changed in those packages.
I’ll work through an example of how to use this tool now:
Using the the Ubuntu 20.04 LTS image kvm optimised image from 20200921 manifest and the Ubuntu 20.04 LTS image kvm optimised image from 20201014 manifest we can find the package version diff.
$ diff 20200921.1-ubuntu-20.04-server-cloudimg-amd64-disk-kvm.manifest 20201014-ubuntu-20.04-server-cloudimg-amd64-disk-kvm.manifest
<snip>
426c426
< python3-apport 2.20.11-0ubuntu27.8
---
> python3-apport 2.20.11-0ubuntu27.9
446c446
< python3-distutils 3.8.2-1ubuntu1
---
> python3-distutils 3.8.5-1~20.04.1
</snip>
This snippet above is a subset of the packages that changed but you can easily see the version changes. Full diff available @ https://pastebin.ubuntu.com/p/mzVBzfC5tw/ .
To see the actual changelog for those package version changes…
$ #install ubuntu-cloud-image-changelog
$ sudo snap install ubuntu-cloud-image-changelog
$ ubuntu-cloud-image-changelog --from-manifest=20200921.1-ubuntu-20.04-server-cloudimg-amd64-disk-kvm.manifest --to-manifest=20201014-ubuntu-20.04-server-cloudimg-amd64-disk-kvm.manifest
<snip>
Snap packages added: []
Snap packages removed: []
Snap packages changed: ['snapd']
Deb packages added: ['linux-headers-5.4.0-1026-kvm', 'linux-image-5.4.0-1026-kvm', 'linux-kvm-headers-5.4.0-1026', 'linux-modules-5.4.0-1026-kvm', 'python3-pexpect', 'python3-ptyprocess']
Deb packages removed: ['linux-headers-5.4.0-1023-kvm', 'linux-image-5.4.0-1023-kvm', 'linux-kvm-headers-5.4.0-1023', 'linux-modules-5.4.0-1023-kvm']
Deb packages changed: ['alsa-ucm-conf', 'apport', 'bolt', 'busybox-initramfs', 'busybox-static', 'finalrd', 'gcc-10-base:amd64', 'gir1.2-packagekitglib-1.0', 'language-selector-common', 'libbrotli1:amd64', 'libc-bin', 'libc6:amd64', 'libgcc-s1:amd64', 'libpackagekit-glib2-18:amd64', 'libpython3.8:amd64', 'libpython3.8-minimal:amd64', 'libpython3.8-stdlib:amd64', 'libstdc++6:amd64', 'libuv1:amd64', 'linux-headers-kvm', 'linux-image-kvm', 'linux-kvm', 'locales', 'mdadm', 'packagekit', 'packagekit-tools', 'python3-apport', 'python3-distutils', 'python3-gdbm:amd64', 'python3-lib2to3', 'python3-problem-report', 'python3-urllib3', 'python3.8', 'python3.8-minimal', 'secureboot-db', 'shim', 'shim-signed', 'snapd', 'sosreport', 'zlib1g:amd64']
</snip>
<snip>
======================================================================
python3-apport changed from version '2.20.11-0ubuntu27.8' to version '2.20.11-0ubuntu27.9'
Source: apport
Version: 2.20.11-0ubuntu27.9
Distribution: focal
Urgency: medium
Maintainer: Brian Murray < - >
Timestamp: 1599065319
Date: Wed, 02 Sep 2020 09:48:39 -0700
Changes:
apport (2.20.11-0ubuntu27.9) focal; urgency=medium
.
[ YC Cheng ]
* apport/apport/hookutils.py: add acpidump using built-in
dump_acpi_tables.py. (LP: #1888352)
* bin/oem-getlogs: add "-E" in the usage, since we'd like to talk to
pulseaudio session and that need environment infomation. Also remove
acpidump since we will use the one from hook.
.
apport (2.20.11-0ubuntu27.8) focal; urgency=medium
.
[Brian Murray]
* Fix pep8 errors regarding ambiguous variables.
======================================================================
python3-distutils changed from version '3.8.2-1ubuntu1' to version '3.8.5-1~20.04.1'
Source: python3-stdlib-extensions
Version: 3.8.5-1~20.04.1
Distribution: focal-proposed
Urgency: medium
Maintainer: Matthias Klose <->
Timestamp: 1597062287
Date: Mon, 10 Aug 2020 14:24:47 +0200
Closes: 960653
Changes:
python3-stdlib-extensions (3.8.5-1~20.04.1) focal-proposed; urgency=medium
.
* SRU: LP: #1889218. Backport Python 3.8.5 to 20.04 LTS.
* Build as well for 3.9, except on i386.
.
python3-stdlib-extensions (3.8.5-1) unstable; urgency=medium
.
* Update 3.8 extensions and modules to the 3.8.5 release.
.
python3-stdlib-extensions (3.8.4-1) unstable; urgency=medium
.
* Update 3.8 extensions and modules to the 3.8.4 release.
.
python3-stdlib-extensions (3.8.4~rc1-1) unstable; urgency=medium
.
* Update 3.8 extensions and modules to 3.8.4 release candidate 1.
.
python3-stdlib-extensions (3.8.3-2) unstable; urgency=medium
.
* Remove bytecode files for 3.7 on upgrade. Closes: #960653.
* Bump debhelper version.
.
python3-stdlib-extensions (3.8.3-1) unstable; urgency=medium
.
* Stop building extensions for 3.7.
* Update 3.8 extensions and modules to 3.8.3 release.
======================================================================
</snip>
Above is a snippet of the output where you can see the exact changes made between the two versions. Full changelog available @ https://pastebin.ubuntu.com/p/cJVwVqzfgh/.
I have found this very useful when tracking why a package version changes and also if a package version change includes patches addressing a specific vulnerability.
We don’t yet publish package version manifests for all of our cloud images so to help in generating manifests I published the ubuntu-package-manifest command line utility to easily generate a package version manifest for any Ubuntu or Debian based image or running instance for later use with ubuntu-cloud-image-changelog.
$ sudo snap install ubuntu-package-manifest
$ # This is a strict snap and requires you to connect the system-backup interface
$ # https://snapcraft.io/docs/the-system-backup-interface
$ # to access the host system package list. This is access read-only.
$ snap connect ubuntu-package-manifest:system-data
$ sudo ubuntu-package-manifest
You can even use this on a running desktop install to track package version changes.